Introduction to SIM Swapping Attack
To understand SIM Swapping Attack, lets discuss a scenario. Just imagine that when you wake up in the morning, you notice that your phone has no signals. You try different options and finally restart it. At that point you might be thinking that it might be a simple network issue. But; despite your different kinds of attempts nothing changes. Then, out of curiosity, you attempt to log into your email account, and you get shocked that your password has also been changed without your authorization. Now you are unable to login to you email account. Subsequently, when you open your wallet app, you get further shocked and frustrated to see that all of your money in your account has also gone. At that moment, you begin to realize that something serious has happened. But probably, it’s already too late to realize because all your online asses have been ruined.
This is how a SIM swapping attack is identified by the user. And in 2025, these types of cybercrimes are growing. These types of attacks are becoming more and more dangerous, and are affecting several victims every day.
How does SIM Swapping Attack Works?
SIM swapping attack, which is also called SIM hijacking, is basically a type of cybercrime or online fraud. It occurs when a criminal succeeds to convince mobile carrier that he is the real owner of the number. Then he requests to issue a new SIM card against the targeted phone number.
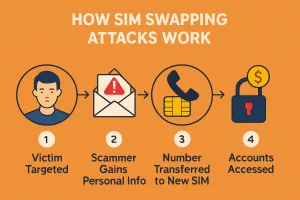
Once a new SIM card is issued, they gain control of the number. That is the time when they start receiving your calls and text messages. As you know text messages may also include verification codes (OTPs), which are used to protect online accounts. From that point, they start accessing your online accounts and other digital life.
Few Real World Cases of SIM Swapping Attacks:
- In 2023, Joe Vezzani, CEO of the crypto platform LunarCrush, was targeted through SIM swap attack. First thing he noticed was that his phone unexpectedly lost signals. Within minutes, hackers gained access to his cryptocurrency wallet and transferred the investments out of his wallet. This attack caused loss of Millions of Dollars to the CEO.
- Recently, in 2025, cybersecurity firm Group-IB disclosed a coordinated SIM swapping racket. This racket was operating in Southeast Asia. This group targeted tech founders and investors. They used stolen data and employees of the Telecom companies to issue replaced SIM cards. The group succeeded to steal over $5 million through unauthorized SIM swaps. For more details about the racket you can Read Group-IB’s full report on SIM swap fraud.
How SIM Swapping Works: Step-by-Step Process
- Information Gathering
The attacker collects personal data of the target person. Personal which they collect includes full name, phone number, address, and his/her ID. Normally all this information is collected from social media or data breaches. They even collect biometrics of the target from dark web.
- Contacting the Mobile Provider
They call mobile service provider of the target person and pretend to be the person. Then they claim that they’ve lost their phone; therefore, they need a new SIM card of the same number.
- Convincing the Representative
Using your personal information (which they already have), they convince the customer service representative to activate a new SIM card.
- Taking Over Your Number
Your number is now active on their SIM. Your phone stops receiving messages, and they start receiving your 2FA codes and OTPs.
- Accessing Your Accounts
They immediately reset passwords, bypass verification steps, and drain your accounts, especially your online banking and crypto wallets.
Why is SIM Swapping a Threat in 2025?
Despite growing awareness, SIM swapping attacks are still successful because:
- Many people still rely on SMS-based 2FA, which is vulnerable.
- Telecom security gaps persist in many countries.
- Attackers now use AI tools to mimic voices or craft more convincing social engineering scripts for phishing.
- Some employees at telecom companies are bribed or coerced to become a partner in the fraud.
According to the FBI, in 2022, Americans lost $72 million due to SIM swap attacks. That number has increased in the last two years because digital assets have become more mainstream. FBI Report on SIM Swapping Losses (external link)
How to Protect Yourself from SIM Swapping
Upgrade from SMS-based 2FA
With the evolution of cybercrime, protective measures have also been upgraded. Therefore, inspite of using SMS based 2FA, adopt authenticator apps (e.g., Google Authenticator) or hardware tokens like YubiKey for better protection.
Set a SIM PIN
Ask your mobile provider to enable a SIM card lock.
Be Vigilant in Case of No Signals
If your phone suddenly loses signal and others in your vicinity don’t, act fast. Immediately call your provider and freeze your accounts.
Avoid Personal Information Online
Avoid posting your phone number, birthdate, or other identifying details on public platforms and social media.
Separate Email Accounts
Use different emails for banking, crypto, and social media apps. This reduces your risk if one account is compromised.
Conclusion
These days mobile number is more than a way to stay connected. It is a gateway to the whole of your online identity. That is the reason that SIM swapping is considered to be a powerful tool for cybercriminals.
Even in 2025 so far, SIM swapping has caused millions of dollars losses to the victims. Moreover, it takes countless hours of recovery of your accounts and personal data.
So take a few moments to review your account settings, upgrade your 2FA methods. Moreover, for protection from SIM swapping, ensure that your mobile provider activates extra layers of protection (like SIM code). Today your little effort can save you from a huge digital disaster tomorrow in shape of SIM swapping.
Learn More About Related Cyber Threats
To build a stronger defense, it is important to understand the broader landscape of online threats. Many SIM swapping cases begin with phishing or social engineering scams. Using these techniques attackers manipulate victims into giving away key their personal details. Learn how to recognize and avoid these traps in our blog on Advanced Phishing and Social Engineering Attacks.
In addition, SIM swapping has already featured in several High-Profile Cybercrime Cases in 2025. You can read out my previous blog to see how such schemes play role in real life.



